Phishing Simulation Attack
Phishing simulation is a training method to help people and organizations spot and avoid phishing attacks. It uses realistic scenarios that imitate tactics used by cybercriminals to trick individuals into sharing sensitive information like usernames, passwords, or financial details.
The main objective of phishing simulation is to educate and increase awareness about the risks of phishing attacks, empowering individuals to make smart decisions when dealing with suspicious emails or messages.


Problems
- No ContextPhishing simulations are often conducted without providing adequate context to employees. In real life individuals might receive suspicious-looking emails in specific situations that make them more vulnerable.
- Lack of RealismSome phishing simulations may lack realism in mimicking actual attacks. Employees participating in simulations can easily identify phishing emails or messages because they don't closely resemble real threats.
- Lack of Impact MeasurementSome phishing simulation programs may provide insufficient information about the actual impact of employees' actions.
- Individual FocusPhishing simulations often concentrate on individual responses, while real phishing attacks may involve team or departmental collaboration. This can result in an incomplete understanding of how well an organization can defend against phishing.
- Limitations in Handling Multi-Vector AttacksSome phishing simulations may only address one attack vector (e.g., email), while real phishing attacks may involve various channels such as text messages or social media.
Benefits
- Provide Adequate ContextOffer background information or context around simulated phishing scenarios to create a more authentic experience.
- Measure Impact RealisticallyDevelop metrics that go beyond simple success or failure indicators. Measure the impact of successful phishing simulations in terms of potential data exposure, financial loss, or reputational damage.
- Team-Based SimulationsIntroduce simulations that involve collaboration among team members or departments. This provides a more holistic view of an organization's ability to collectively respond to phishing threats.
- Multi-Vector SimulationExpand simulations to cover various attack vectors, including emails, text messages, and social engineering attempts.
- Emphasize Learning over EvaluationUtilizing phishing simulations is a valuable method for ongoing learning, fostering a culture of cybersecurity awareness
Collected Information
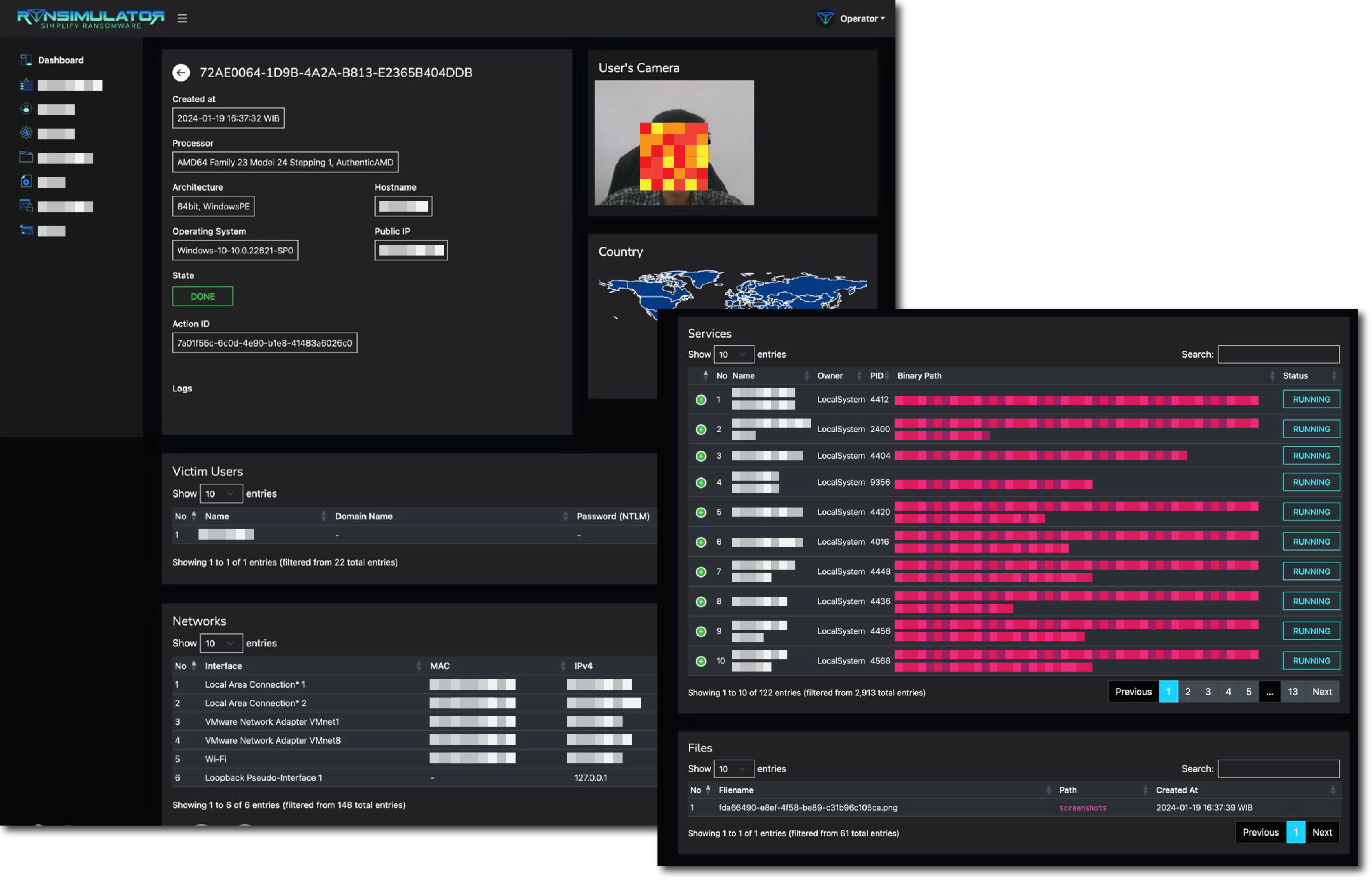
Basic
- Message Opened
- Clicked Link
- Submitted Data
Technical
- Username
- Device Architecture
- Operating System
- IP Address
- Network Interface
- Geolocation
- Desktop Screenshoot
- Camera